

Weak passwords are one of the easiest ways cybercriminals gain unauthorized access to your device and accounts.
o Create passwords with at least 12 characters, including uppercase, lowercase, numbers, and special symbols.o Avoid using obvious choices like birthdays, names, or common words.o Enable biometric authentication (e.g., fingerprint or facial recognition) for an extra layer of security.
o Use a password manager to store and manage your complex passwords securely.
Even if someone manages to steal your password, 2FA acts as a second line of defense.
o Activate 2FA on all accounts (e.g., email, social media, banking). o Use an authentication app (e.g., Google Authenticator or Authy) instead of SMS for better security.
o Avoid sharing your 2FA codes with anyone, even if they claim to be from a trusted organization.


Cybercriminals exploit vulnerabilities in outdated software to gain access to your device.
o Enable automatic updates for your operating system and all apps. o Use an authentication app (e.g., Google Authenticator or Authy) instead of SMS for better security.
o Check updates manually if automatic updates are not enabled.
Security apps can detect malware, phishing attempts, and other cyber threats.
o Download security apps only from official app stores (e.g., Google Play Store, Apple App Store). o Choose apps with high ratings and positive reviews.
o Run regular virus and malware scans on your device.


Public Wi-Fi networks are often unsecured, making it easy for hackers to intercept your data.
o Use a VPN (Virtual Private Network) to encrypt your internet traffic. o Avoid accessing sensitive accounts (e.g., banking apps) on public Wi-Fi.
o If a VPN isn’t available, use your mobile data network for sensitive activities.
Phishing attacks often use fake links and attachments to install malware or steal information.
o Don’t click on links or download files from unknown sources. o Verify the sender’s identity before interacting with emails, messages, or attachments.
o Look for HTTPS in website URLs to ensure they are secure.

Unsecured Bluetooth connections and location services can be exploited by hackers.
o Turn off Bluetooth and location services when not actively using them. o Avoid pairing your device with unknown or public Bluetooth connections.
o Use device settings to restrict location access to only essential apps.
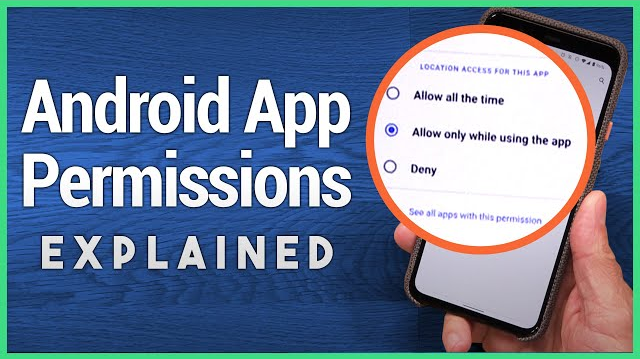
Many apps request unnecessary permissions that could compromise your privacy.
o Regularly review app permissions in your phone settings. o Only grant permissions that are necessary for the app's core functions.
o Be wary of apps asking for access to your contacts, camera, or messages unnecessarily.

Unauthorized transactions on banking apps or digital wallets can indicate fraud.
o Enable real-time transaction alerts from your bank. o Regularly review your account statements and look for unusual activity.
o Immediately report any suspicious activity to your bank.
Knowledge is your best defense against cyber scams.
o Stay informed about common scams like phishing, smishing (SMS phishing), and fake tech support calls. o Follow cybersecurity news and updates from reliable sources.
o Share what you’ve learned with friends and family to help them stay safe too.
